Payload Generation
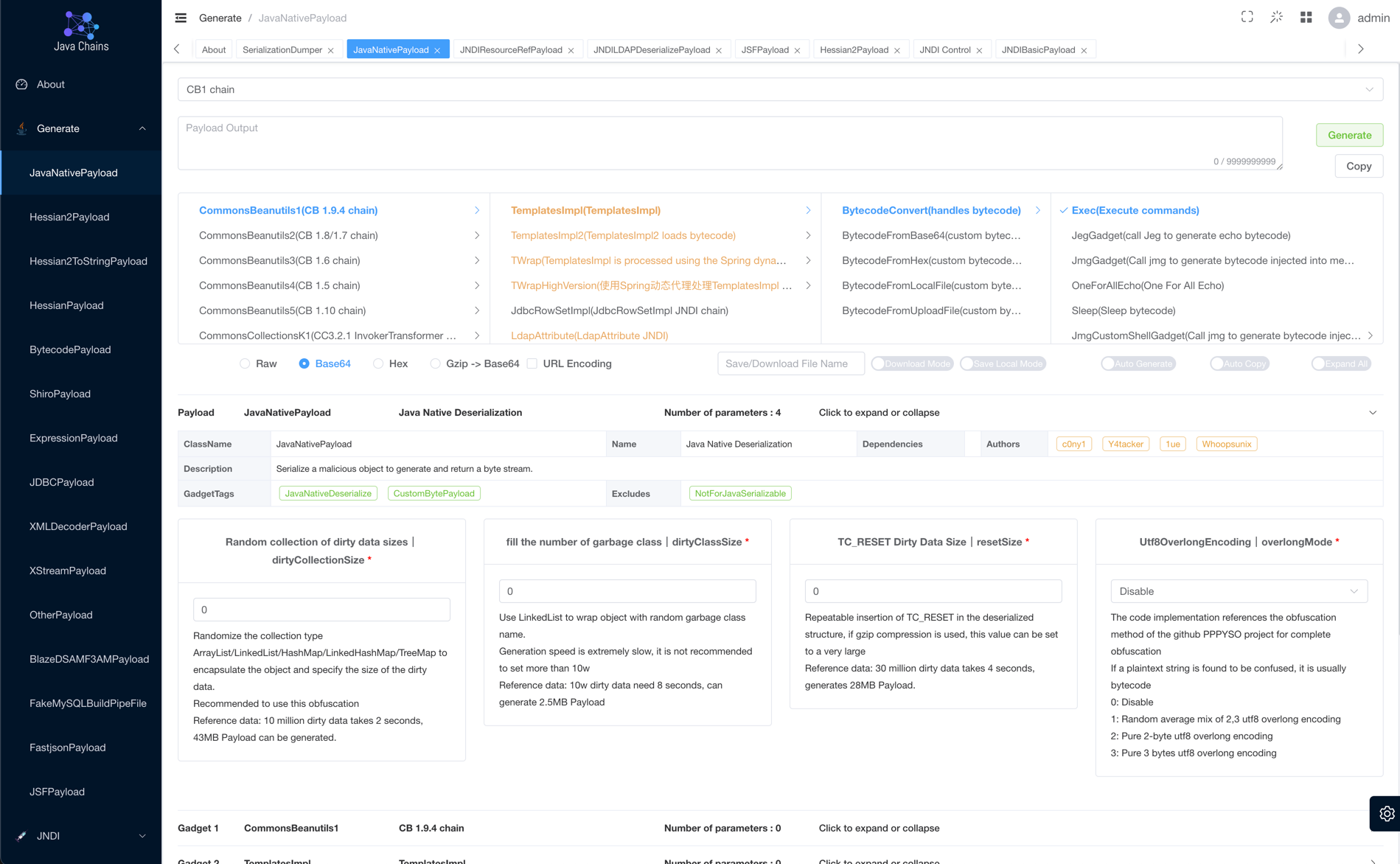
JavaNativePayload
Java deserialization native Payload generation.
Some commonly used chains are displayed:
- CB Chain: CommonsBeanutils 19.x, CommonsBeanutils 18.x, CommonsBeanutils 1.6 versions
- CC Chain: CommonCollection K1, CommonCollection K2, CommonCollection K3, CommonCollection K4
- JSON-related chains: Fastjson1, Fastjson2, Jackson
- Secondary deserialization related: SignedObject secondary deserialization, RMIConnector secondary deserialization, C3p0 secondary deserialization
- DataSource related chains: A total of 13 different versions and different classes of getter exploitation
- C3p0: JNDI chain, secondary deserialization chain, native class loading chain, supporting two different SUID versions
- FindClass dnslog detection class, collecting most gadget classes online, can detect 100+ classes. Canary is inserted in the detection payload to assist in determining which classes are blacklisted, causing detection failure. Supports manual setting, file reading, and custom batch detection classes.
HessianPayload
HessianPayload: Hessian1 deserialization Payload generation, and supports HessianServlet format deserialization data.
Hessian2Payload: Hessian2 deserialization Payload generation.
- Supports Hessian1 and Hessian2 versions of Payload.
- Some Hessian chains are displayed as follows:
- SwingLazyValue: JDK native chain loading BCEL
- SwingLazyValue2: JDK native chain triggering JNDI
- SwingLazyValue3 + MethodUtil: JDK native chain executing arbitrary bytecode
- UnixPrintService: JDK native chain, Linux command injection
- UnixPrintServiceLookup: JDK native chain, Linux command injection
- ProxyLazyValue + SerializationUtils: Depends on spring, can achieve secondary deserialization
- SpringAbstractBeanFactoryPointcutAdvisor: Public spring jndi chain
- SpringPartiallyComparableAdvisorHolder: Public spring jndi chain
- Xslt: This chain is integrated, file writing and loading Xslt file to achieve bytecode execution

The generated Hessian deserialization Payload can be applied in xxl-job.

BytecodePayload
Bytecode generation.
- For example, it can generate command execution bytecode, Sleep bytecode, DNSLog bytecode, inject memory horse bytecode, echo bytecode, middleware detection bytecode, write file bytecode, download file bytecode.
- Supports custom bytecode version.
- Supports custom bytecode class name.
- Supports generating TemplatesImpl bytecode format - implements AbstractTranslet interface.
- Supports using Class-Obf for bytecode obfuscation.

ShiroPayload
Shiro Payload generation, convenient for manual generation and testing in some special environments.
- Supports custom AES KEY.
- Supports AES GCM mode.
- Supports inserting Base64 obfuscation characters.
OtherPayload
Some commonly used Payloads are used with the HTTP Server module to achieve reverse connection to the target server. For details, see: HTTP Server Module introduction.
CharsetJar Generation
Suitable for writing charsets.jar RCE in SpringBoot environment.
To directly obtain the jar package, you need to set the format to raw and use "download mode".

References:
ExpressionPayload
Expression Payload generation, essentially replacing the bytecode part in the bytecode template with the expression, manual implementation is recommended.
BcelConvert: BCEL format bytecode generation.JsConvert: Oracle Nashorn JS expression loading bytecode.VelocityConvert: Velocity loads bytecode through bcel.- ...
Payload Obfuscation Support
The Payloads generated by this platform support the following obfuscation scenarios:
| JavaNativePayload | HessianPayload | Hessian2Payload | |
|---|---|---|---|
| Random collection dirty data filling | ✅ | ✅ | ✅ |
| Garbage class filling | ✅ | ✅ | ✅ |
| UTF-8 Overlong Encoding | ✅ | ✅ | ✅ |
| TC_RESET filling | ✅ | ❌ | ❌ |
Note: If you want to use the UserCustomByteArrayFromXXX Gadget to provide custom Java serialized byte stream data for obfuscation, currently, random collection and garbage class insertion obfuscation are not supported. This is related to the implementation of obfuscation, and the specific support is as follows:
| JavaNativePayload (custom serialization scenario) | |
|---|---|
| Random collection obfuscation | ❌ |
| Garbage class insertion | ❌ |
| UTF-8 Overlong Encoding | ✅ |
| TC_RESET filling | ✅ |